SOC Alert Investigation: EventID 114 - Phishing Incident Response Report [SOC114]
Platform: LetsDefend
Alert ID: SOC114
Event ID: 114
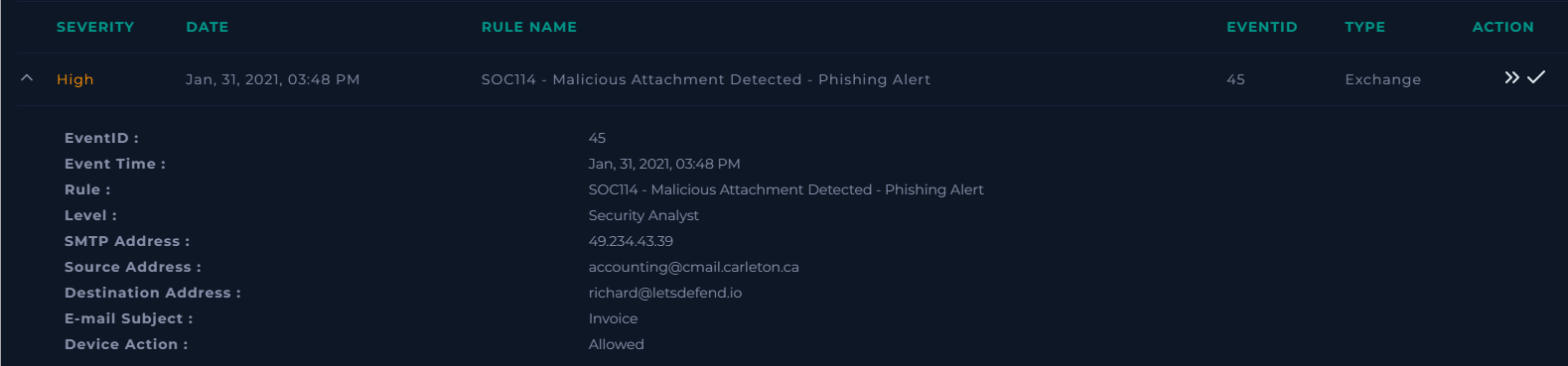
Alert Name: Malicious Attachment Detected - Phishing Alert
Incident Type: Phishing
Event Time: Jan, 31, 2021, 03:48 PM
Incident Summary
| Category | Details |
|---|---|
| Incident Date | Jan, 31, 2021, 03:48 PM |
| Alert Trigger | Malicious Attachment Detected - Phishing Alert |
| Verdict | True Positive |
| Status | Allowed |
Alert Details
Investigation & Triage
A. Email Analysis
Goal: Determine the scope and delivery method.
- Target User:
richard@letsdefend.io - Sender / Source:
accounting@cmail.carleton.ca - SMTP Address: 49.234.43.39
- Delivery Vector:
- Corporate Email (Outlook/Exchange)
- Initial Action:
- Allowed (User accessed the resource)
B. Artifact Analysis (Static & Dynamic)
1. URL / Domain Analysis
- No URL detected
2. File / Attachment Analysis
- File Name or Type:
Excel file - Hash (MD 5/SHA 256):
c9ad9506bcccfaa987ff9fc11b91698d
Sandboxing Results
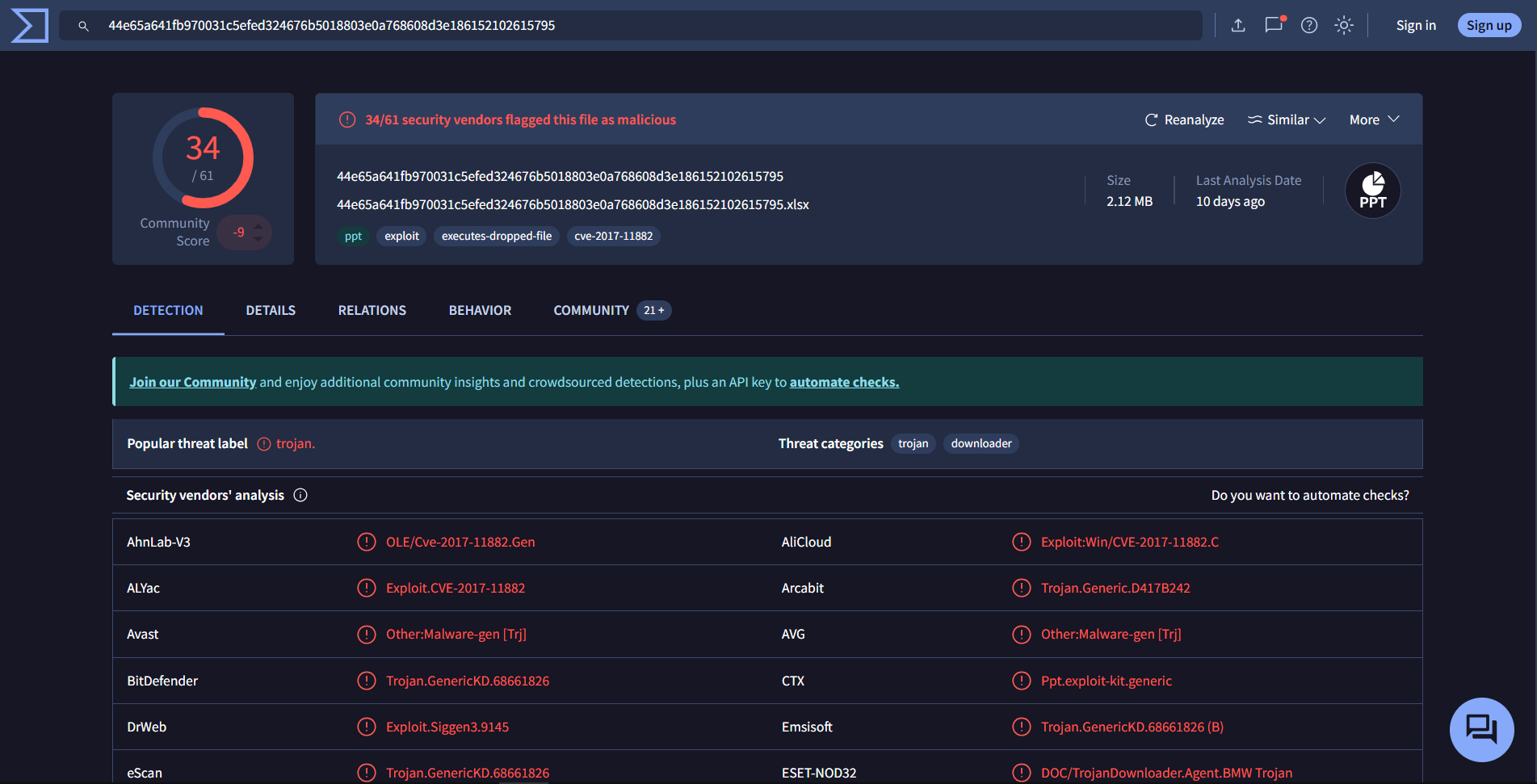
VirusTotal: 34/61 security vendors flagged this file as malicious.
- Popular threat label: trojan
- Threat categories: trojan, downloader
- Exploit: CVE-2017-11882
Network Relations (Contacted URLs): VirusTotal identified the following malicious URLs associated with the file. Note that the scan dates reflect recent analysis activity.
| Scanned Date | Detections | Status | URL |
|---|---|---|---|
| 2025-12-09 | 11/98 | 401 | http://andaluciabeach.net/image/network.exe |
| 2025-11-07 | 1/98 | 401 | http://www.andaluciabeach.net/ |
Contacted Domains:
andaluciabeach.net(Created: 2011-08-29)centourismeadddynamicoptional001.loseyourip.com
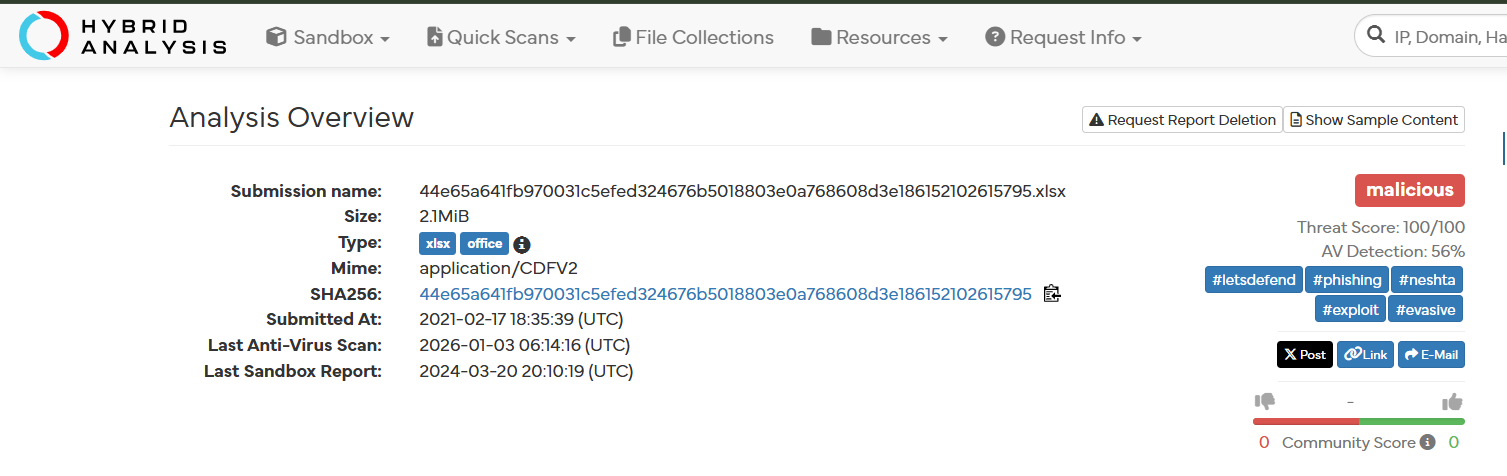
HybridAnalysis: Malicious
- Threat Score: 100/100
- AV Detection: 56%
- Tags: Phishing, Neshta, Exploit, Evasive
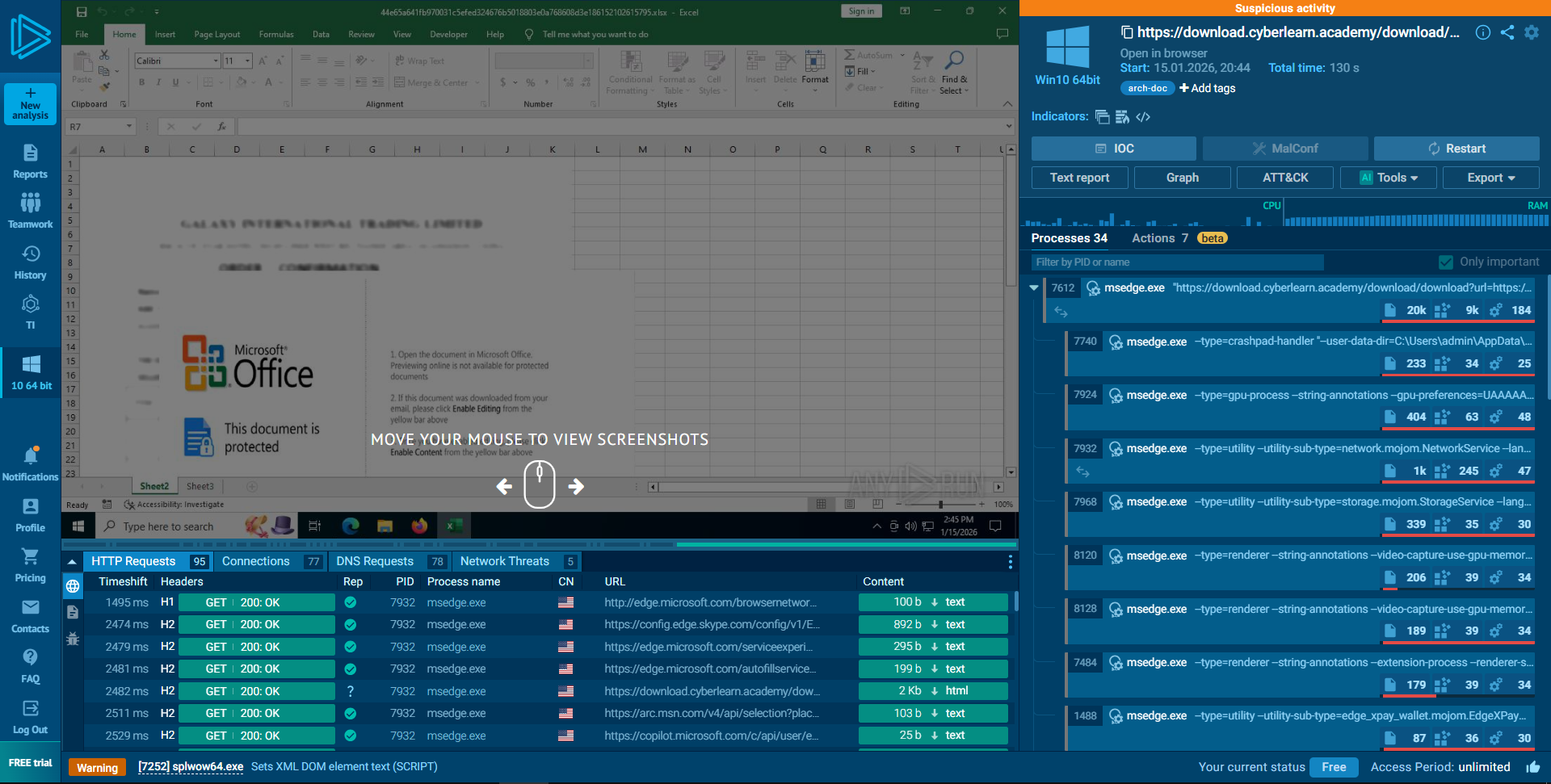
AnyRun: The following sequence occurred immediately after the user accessed the file:
- File Execution: The user opened the file
44e65a641fb970031c5efed324676b5018803e0a768608d3e186152102615795.xlsx. - Process Creation: The
excel.exeprocess was spawned. Windows created standard LNK (shortcut) files in theRecentfolder, confirming user interaction. - Network Beaconing:
excel.exeimmediately initiated an HTTP GET request to an external domain (previews.123rf.com). - Payload Retrieval: The application downloaded a
.jpgimage containing the text “Infected”. - Visual Execution: The downloaded image was rendered within the Excel spreadsheet, providing visual confirmation that the script ran successfully.
3. Exploit Analysis: CVE-2017-11882
- Vulnerability Identified: Microsoft Office Equation Editor Vulnerability.
- Mechanism:
- This is a critical memory corruption vulnerability (stack buffer overflow) in
EQNEDT32.EXE, a legacy component responsible for inserting and editing equations in Microsoft Office documents. - Execution Flow: The malicious Excel file contains a specially crafted equation object. When the user opens the file, the Equation Editor process (
EQNEDT32.EXE) automatically handles this object. Due to the vulnerability, the attacker can overflow the memory buffer and execute arbitrary code (shellcode) without further user interaction. - Result: In this incident, the exploit successfully executed shellcode that triggered the
excel.exeprocess to reach out to the C 2 domain (previews.123rf.com) and download the payload.
- This is a critical memory corruption vulnerability (stack buffer overflow) in
- Significance:
- Although patched by Microsoft in November 2017, this remains one of the most commonly exploited vulnerabilities because
EQNEDT32.EXEwas compiled without modern security protections (like ASLR and DEP), making it a reliable entry point for attackers if the system is not fully patched.
- Although patched by Microsoft in November 2017, this remains one of the most commonly exploited vulnerabilities because
Impact Assessment (Endpoint Correlation)
Goal: Did the attack succeed? (Check EDR/Sysmon/Proxy Logs)
| Check | Result | Evidence |
|---|---|---|
| Network | Connected | The host successfully established an outbound connection to previews.123rf.com and retrieved the image payload (Status: 200 OK). |
| Process | Spawned | excel.exe launched successfully. Note: No malicious child processes (like cmd.exe or powershell.exe) were observed; the malicious activity occurred directly within the Excel process context. |
| File | Dropped | The malicious file 44e65a64... .xlsx was written to C:\Users\admin\Downloads\. Temp files were also created in AppData as Excel ran. |
Timeline of Events:
20:19:08- User Execution: The user (or simulation script) executes the downloaded file44e65a64... .xlsxfrom the Downloads folder.20:19:10- Process Start: The processexcel.exeinitializes and opens the document.20:19:12- Malicious Event:excel.exeinitiates an HTTP GET request tohttps://previews.123rf.com/.../infected...jpg, successfully downloading and rendering the “Infected” image stamp.
Containment & Eradication
- Isolation: Device isolated from network.
- Cleanup: Malicious file and mail were deleted.
Indicators of Compromise (IOCs)
Use these for threat hunting across the rest of the network.
- IPv 4:
49.234.43.39(Sender IP) - Domains:
andaluciabeach.netpreviews.123rf.com(Payload Drop URL)
- Hashes (SHA 256):
44e65a641fb970031c5efed324676b5018803e0a768608d3e186152102615795 - Sender:
accounting@cmail.carleton.ca - Subject:
Invoice
MITRE ATT&CK Mapping
- T 1566.001: Phishing: Spearphishing Attachment
- T 1204.002: User Execution: Malicious File
- T 1203: Exploitation for Client Execution (Exploits CVE-2017-11882 in Microsoft Equation Editor)
Analysis Date: January 15, 2025
Analyst: El OMARI Zakaria