SOC Alert Investigation: EventID 82 - Phishing Mail Detected [SOC140]
Platform: LetsDefend
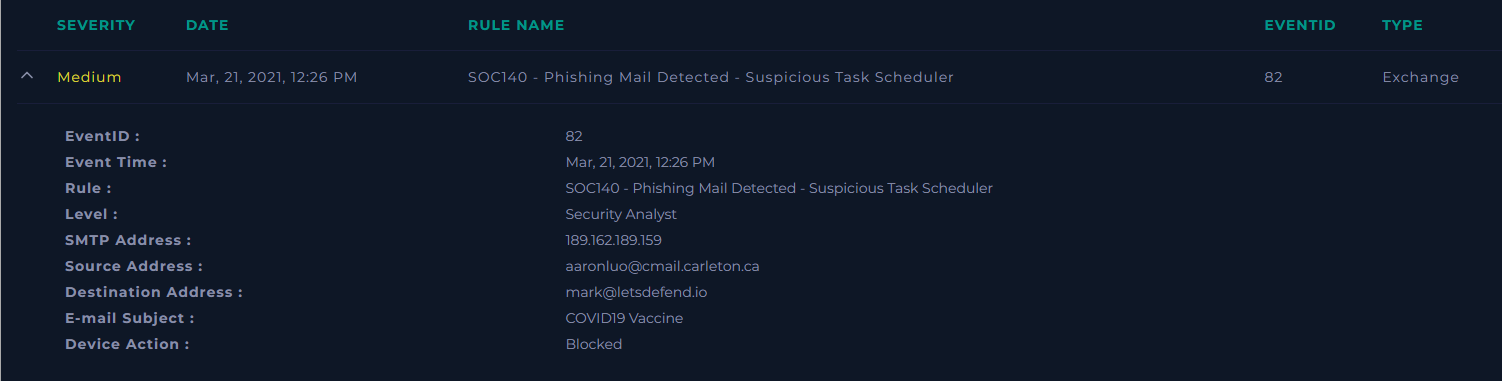
Alert ID: SOC140
Event ID: 82
Alert Name: Phishing Mail Detected - Suspicious Task Scheduler
Incident Type: Email / Phishing / Malware
Event Time: Mar, 21, 2021, 12:26 PM
Incident Summary
| Category | Details |
|---|---|
| Incident ID | SOC 140 |
| Alert Rule | Phishing Mail Detected - Suspicious Task Scheduler |
| Event Time | Mar, 21, 2021, 12:26 PM |
| Severity | Medium |
| Verdict | True Positive (Blocked Attempt) |
Alert Details
The alert originated from the Email Gateway, triggering on suspicious task scheduler activity associated with a phishing email targeting user Mark.
Investigation & Triage
A. Email Analysis
The alert originated from the Email Gateway. A suspicious email was detected targeting the user Mark.
Email Metadata
- Sender:
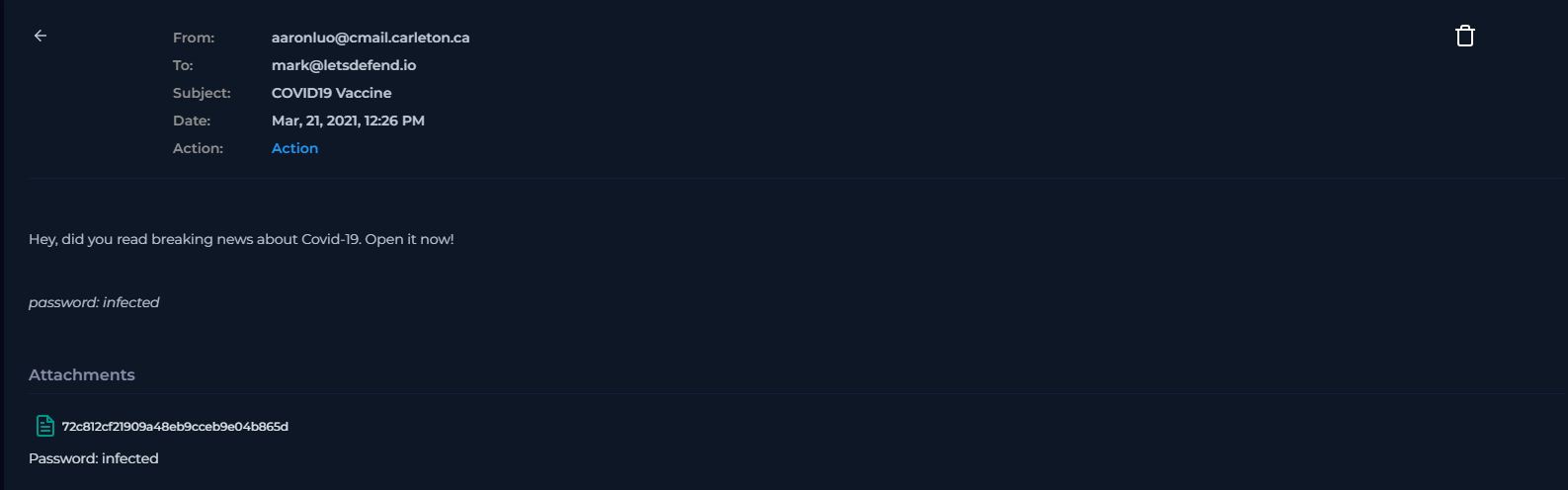
aaronluo@cmail.carleton.ca(Likely a compromised academic account). - Subject:
COVID19 Vaccine(Lure: Health/Fear). - Recipient:
mark@letsdefend.io - Action Taken: Blocked (The email was stopped before delivery).
Suspicious Indicators
- Urgency: “Open it now!”
- Evasion: The body contained
password: infected. Attackers password-protect archives to prevent automated scanners from inspecting the files inside.
B. Artifact Analysis (The Payload)
We extracted the attachment hash from the alert logs to perform deep analysis.
- Attachment Name:
72c812cf21909a48eb9cceb9e04b865d.zip - Malicious File Inside:
Material.pdf(Actually an Executable). - MD5:
72c812cf21909a48eb9cceb9e04b865d
1. Threat Intelligence Results
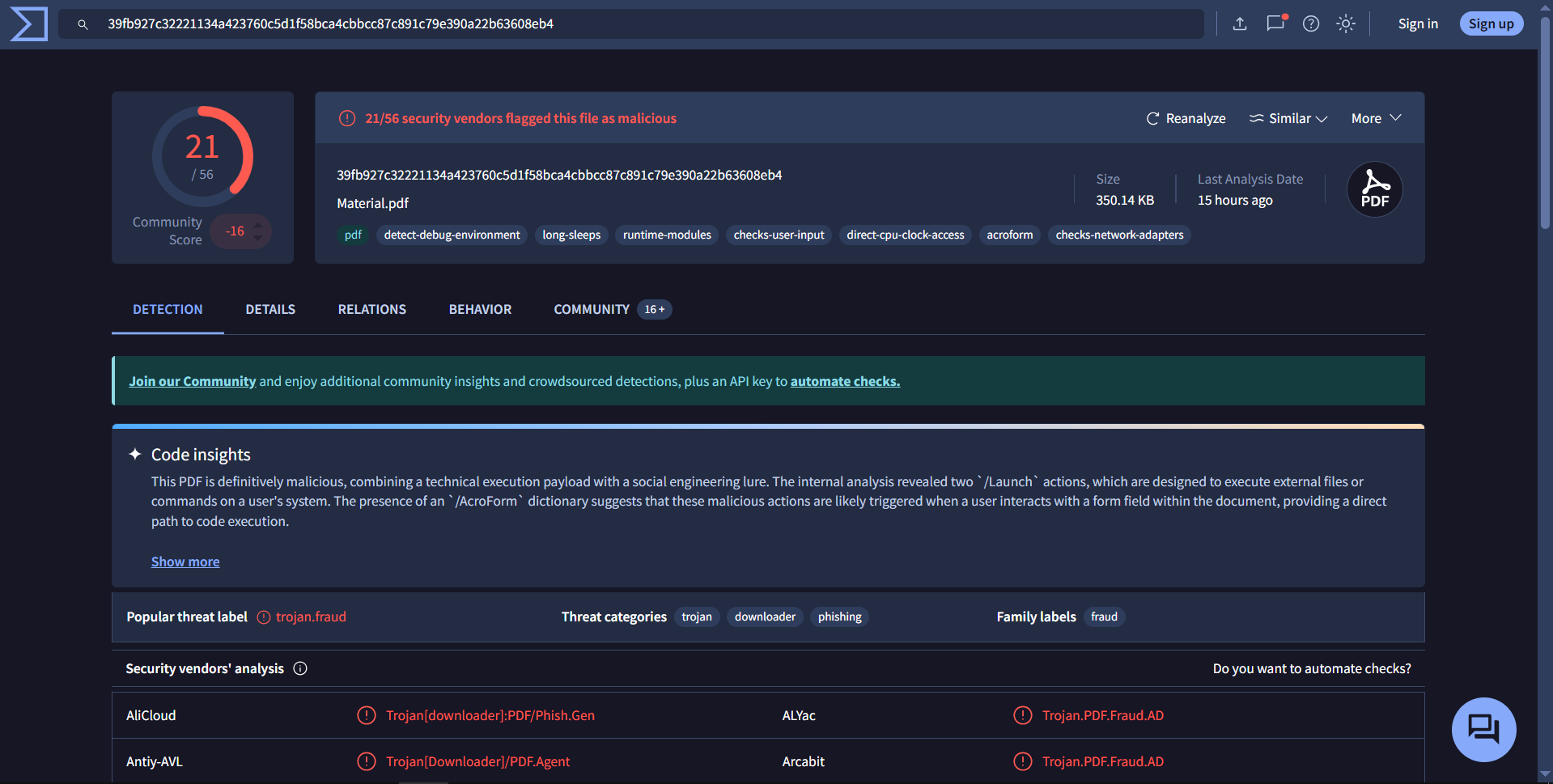
VirusTotal Analysis
- VirusTotal: 21/56 security vendors flagged this file as malicious.
- Popular Threat Label: Trojan.Fraud
- Threat Categories: Trojan, Downloader, Phishing
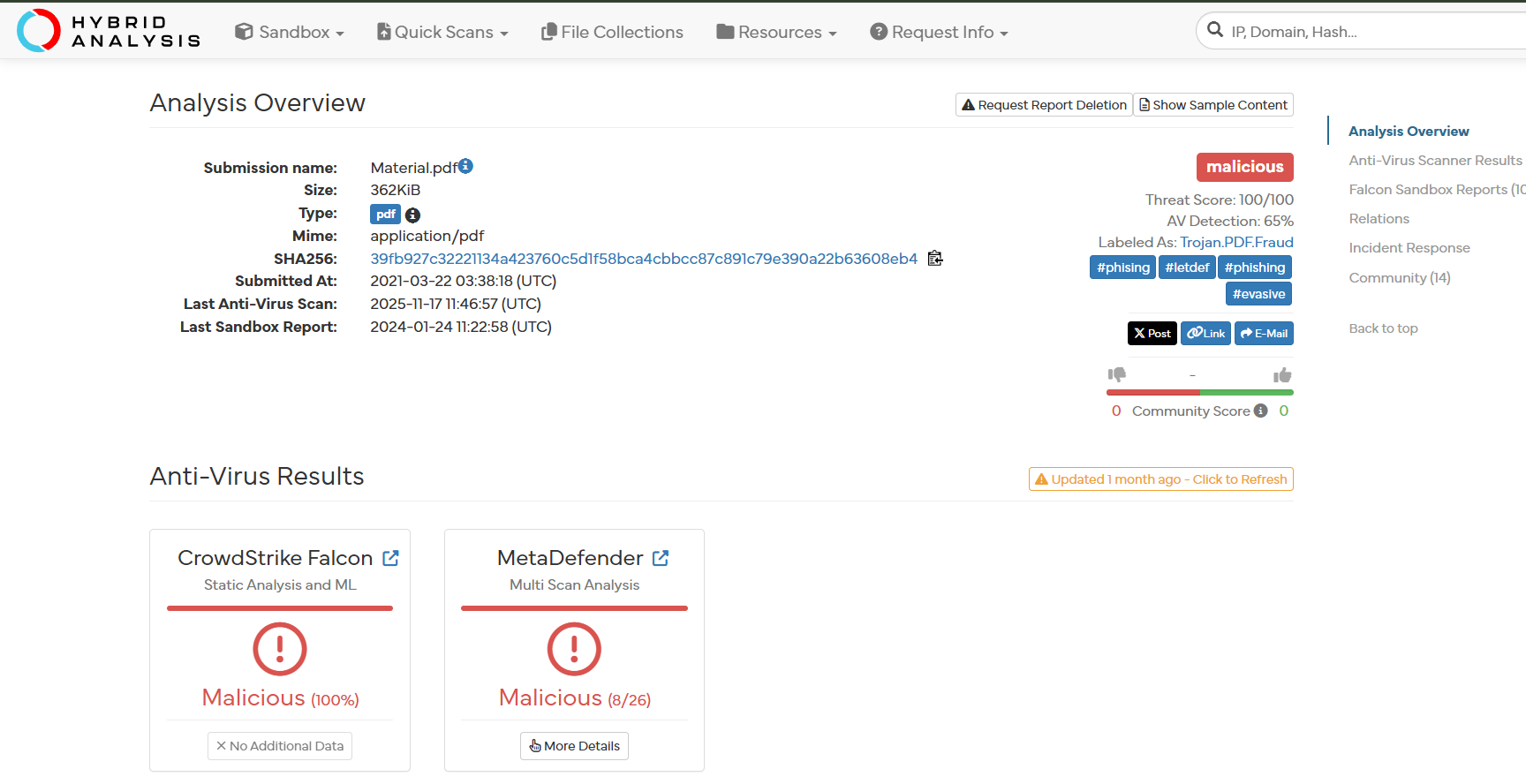
Hybrid Analysis
- HybridAnalysis: Malicious Verdict.
- Threat Score: 100/100
- AV Detection: 65%
- Labeled As: Trojan.PDF.Fraud
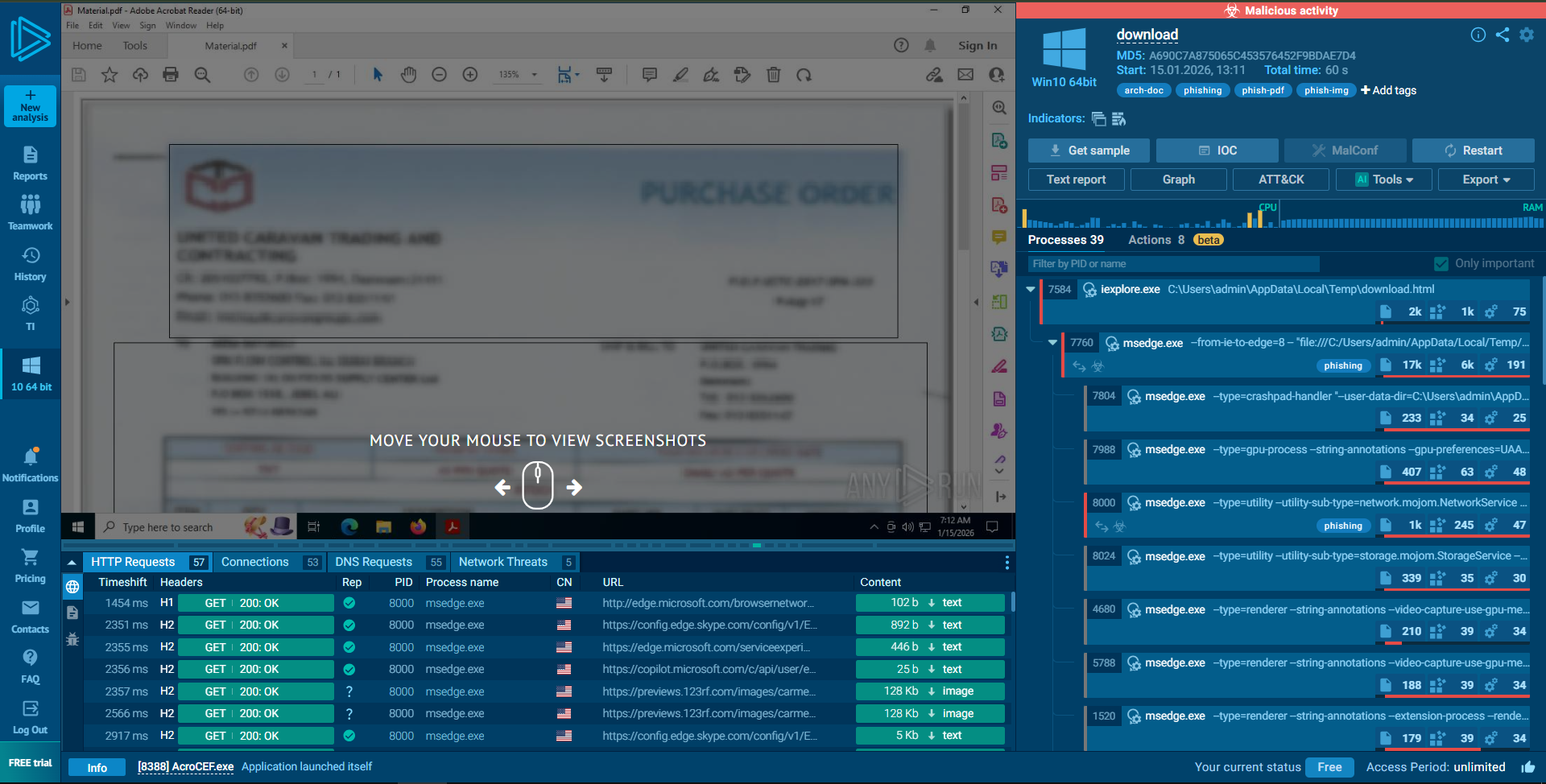
2. Dynamic Analysis (Sandbox Behavior - ANY.RUN)
The malware was executed in a controlled sandbox environment. The following behaviors were observed:
Execution Chain
- The user downloads the ZIP from
download.cyberlearn.academy. - The file
Material.pdfis extracted and executed. - LodaRAT Behavior: The process masquerades as a PDF but executes AutoIT scripts to initiate network connections.
Network Activity (C2)
- Initial Download:
https://download.cyberlearn.academy/download/download...(Redirects to AWS S3 bucket). - Command & Control: Immediate connection to
https://a.pomf.cat/hgfetb.R11. This is a “dead drop” resolver used to fetch the next stage payload or configuration. - IP Connection: Traffic observed to
3.5.129.36.
Dropped Files & Indicators
C:\Users\admin\Downloads\...\Material.pdf- Temporary files created in Edge User Data folders (e.g.,
load_statistics.db-wal), indicating the malware attempts to interact with or steal browser data.
Malware Identification
- Sandboxing Results (ANY.RUN): The file
Material.pdfis an AutoIT compiled executable. - Malware Family: LodaRAT (Loda).
- Behavior Observed:
- C2 Connection: The malware reached out to
https://a.pomf.cat/hgfetb.R11to download a secondary stage/config. - Persistence: It executed
schtasks.exe(Task Scheduler) to ensure it runs automatically on reboot. This behavior matches the alert rule “Suspicious Task Scheduler.”
- C2 Connection: The malware reached out to
Impact Assessment
- Did the user receive the email? No. The gateway status is Blocked.
- Did the malware execute? No. Endpoint logs for Mark show no traffic to
pomf.catand no processes namedMaterial.pdf.
Indicators of Compromise (IOCs)
| Type | Value | Description |
|---|---|---|
| C2 Domain | a.pomf.cat | Hosted the second-stage payload. |
| C2 URL | https://a.pomf.cat/hgfetb.R11 | Specific malware resource. |
| File Hash (MD5) | 72c812cf21909a48eb9cceb9e04b865d | The malicious ZIP attachment. |
| File Hash (SHA256) | 39fb927c32221134a423760c5d1f58bca4cbbcc87c891c79e390a22b63608eb4 | The dropped executable (Material.pdf). |
Mitigation & MITRE ATT&CK
Current Status: The threat was neutralized at the gateway. No further action is required on the endpoint.
MITRE ATT&CK Mapping
- T1566.001 (Phishing: Spearphishing Attachment): The delivery vector via email.
- T1027.013 (Obfuscated Files or Information: Encrypted/Compressed): Using a password-protected ZIP to hide the malware.
- T1053.005 (Scheduled Task/Job: Scheduled Task): The malware’s method for persistence (LodaRAT signature).
- T1036.008 (Masquerading): Naming the executable
Material.pdfto trick the user.
Analysis Date: January 15, 2025
Analyst: El OMARI Zakaria